No matter where you work, whether it’s in a regular office, a home office, on your iPhone, or on the road, a virtual private network (VPN) is one of the most effective methods to protect yourself from data breaches on the internet, particularly while utilizing public wi-fi networks. However, how effective are VPNs, and which VPN is the most appropriate for you? What are the disadvantages of utilizing a Virtual Private Network (VPN)? All of your VPN-related questions will be answered in our executive guide, including some that you probably didn’t even know you needed to ask.
So, what is VPN? Why do you need a VPN, and how to choose the right one? Find out how to choose the perfect VPN solution on PrivacyJournal.
Let’s explore!
What is VPN?
In computer networking, a Virtual Private Network (VPN) is a form of network that imitates the behavior of a private network across a public network.
The goal of a virtual private network (VPN) is to protect your identity and privacy when communicating over the internet.
The difficulty with the internet is as follows: It’s essentially insecure from the start. When the internet was initially created, it was important to be able to transfer packets (chunks of data) as consistently as possible, and this was the highest priority. Networking throughout the nation and across the globe was still in its infancy, and nodes were often offline. In order to avoid failure, the vast majority of the internet’s essential protocols (communication techniques) were created rather to transmit safe data.
The programs you’re used to utilizing, such as email, the web, instant messaging, Facebook, and so on, are all built on top of the Internet Protocol (IP) core that you’ve come to know and love. Despite the fact that certain standards have been created, not all internet applications are secure. Many people continue to transfer their information without any security or privacy protection at all.
Any internet user becomes susceptible to criminals who could steal your financial or credit card information, governments who might want to listen in on their people’s conversations, and other internet users who might wish to spy on you for a variety of unscrupulous purposes.
A virtual private network (VPN) builds a secure tunnel across the public internet. In theory, everything you communicate is encased in this private communications channel and encrypted, making it impossible for anybody to interpret your messages even if your packets are intercepted and decoded. Despite the fact that VPNs are strong and necessary tools for protecting yourself and your data, they do have certain limits.
How does VPN work?
Let us begin with the most fundamental concept of internet communication. Consider the following scenario: you’re sitting at your desk and you want to view a website such as ZDNet. In order to do this, your computer sends a series of packets to commence a request. If you’re working in an office, those packets are likely to pass via switches and routers on your local area network (LAN) before being sent to the public internet through a router.
Once on the public internet, the packets pass through a slew of computers before arriving at their destination. It is necessary to make a separate request to a series of name servers in order to convert the DNS name ZDNet.com into an IP address. That information is returned to your browser, which then sends the request out to a large number of machines connected to the public internet once again. At some point, it will reach the ZDNet infrastructure, which will also route those packets, fetch a web page (which is made up of a number of different pieces), and deliver the whole thing back to you.
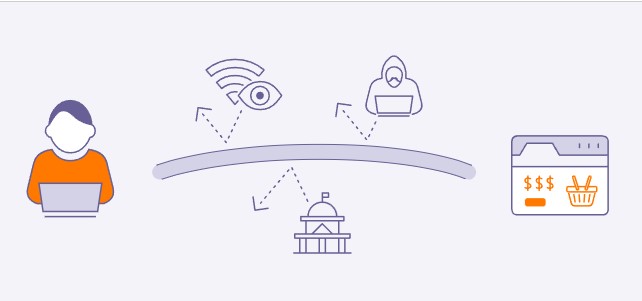
Each internet request is often followed by a sequence of communication events between many sites. In order for a VPN to function, those packets must first be encrypted before they can be sent. This process frequently involves disguising both the contents and the information about your originating IP address. The VPN software installed on your computer then transmits those packets to a VPN server located at a remote location, where the information is decrypted.
Understanding the location of the VPN server’s endpoint is one of the most crucial aspects of comprehending the limitations of virtual private networks. That will be the subject of our next discussion.
Do VPNs Keep You Safe Online?
An encrypted virtual private network (VPN) can conceal the contents of your web traffic from certain observers and may make it more difficult for you to be followed online when you use one. However, a virtual private network (VPN) may only give limited security against the kind of risks you’re most likely to face on the internet, such as malware, social engineering schemes, and phishing sites.
There are more effective approaches to deal with these dangers. Keep in mind that your browser, as well as most antivirus programs, have built-in mechanisms for identifying phishing sites, so pay attention when you notice a warning. In the event that you notice a suspicious pop-up window or get an unexpected email that asks you to take some action, use your common sense. Rather of reusing and using weak passwords, you should invest in a password manager that will create and store unique and complicated passwords for each site and service that you use. Protect your online accounts by enabling multi-factor authentication everywhere it is offered. Last but not least,
Do I Need a VPN?
A few years ago, virtual private networks (VPNs) had a much more clearly defined position in your privacy and security toolset. At the time, the vast majority of communication was sent through HTTP, often without any encryption at all. Nowadays, the vast majority of online traffic is sent using HTTPS, which does, in fact, secure your connection. When looking at HTTPS traffic, an ISP or someone spying on your network can only see the destination at the topmost level of the traffic’s hierarchy.
Advertisers have also gotten more sophisticated in their monitoring attempts in the last few years. Because of browser fingerprinting and other tactics, a VPN’s anonymizing capabilities are limited to a certain extent. However, even the much-heralded capability of virtual private networks to spoof locations, circumvent internet restrictions, and unblock streaming is becoming less guaranteed as firms and governments grow more active in identifying and blocking VPN traffic.

The proliferation of advanced monitoring mechanisms, as well as the use of HTTPS, are often mentioned as reasons why VPNs aren’t worth the investment. However, whether or not you should utilize a VPN is entirely dependent on your needs. Though you want your traffic to look as if it is originating from another nation for any reason, a virtual private network (VPN) will do this. A virtual private network (VPN) may also assist you in making it a bit more difficult for advertising and other third parties to trace your online movements. Furthermore, if you want to guarantee that your ISP knows as little as possible about your internet behavior, a VPN will certainly help you do this.
A virtual private network (VPN) will not make you indestructible on the internet, but it will help you secure your privacy. As with any technology, a VPN is most effective when used in conjunction with other security and privacy measures. However, as with any instrument, it is most effective when used for the intended purpose.

Eyal Ephrat serves as the co-founder and CEO of medCPU.com, where technology is making significant strides in the field of medicine. Through his experience in purchasing PC and laptop equipment and various other tech products, Eyal Ephrat contributes valuable insights to medCPU’s mission.
